Your Neighborhood Technology Success partner
Why Businesses Choose Big Water Tech
Comprehensive IT Solutions
Big Water Technologies offers tailored outsourced IT support solutions covering managed services, phone systems, cybersecurity, cloud services, and more.
Security and Compliance Experts
You can rest assured knowing we're security and compliance experts with the ability to protect your network while ensuring your environment exceeds regulatory requirements.
Exceptional Customer Service
Our team has been in the industry since the 1970s - allowing us to offer you informed, strategic insight while maintaining a high level of customer service.
Commitment to Client Success
You're far too busy to worry about technology. That's why your success is our success. We make IT work for you - so you can drive growth.
Client Success Stories
We currently use Big Water for our managed phone service and they are great! We have had issue with managed phone service providers in the past but Jenn is super responsive when we have an issue or need a new line added or removed. I would not hesitate to recommend Big Water for managed phone services, low voltage or other technology needs!
COLLEEN BUDDE
Franchise Owner at Office Evolution Troy
Is Your Technology Becoming Too Complex
For What It Needs To Be?

John Lowery
CEO, Big Water Tech
Big Water Tech is Here to Help Keep IT Simple with Bespoke IT Services.
At BigWater Technologies, safeguarding the integrity and security of your IT system is non-negotiable. We're dedicated to optimizing your technology to enhance efficiency and power.
Feel like you’ve been down this road before?
If you've felt burned by outsourced IT support providers in the past, rest assured, we prioritize fostering lasting client relationships over maximizing profits. Our focus is on maximizing the potential of your current IT infrastructure while keeping costs in check – possibly even reducing them.
Contact us at (248) 220-7714 to kick-start crucial IT discussions tailored to businesses like yours. Let's redefine your IT experience together.
Schedule an Appointment Today
As Your Technology Success Partner,
We're Here to Help You Drive Growth With:
Simplified IT Management
BIGview offers proactive outsourced IT support and management of technology assets on a subscription basis.
VoIP & Hybrid Phone Systems
Desktop & Mobile App, as well as Service Management with flexible VoIP service.
Vendor Neutral Management
We provide a thorough needs assessment, available provider review, order management, issue management, and regular bill reviews.
Comprehensive Equipment Support
We take care of your network security, switching, WiFi, servers, computers, video conferencing, and more.
Installation & Support
Low voltage cabling, paging, and camera systems designed to fit the needs of your team.
Ongoing Evaluation and Planning
Stay focused on the success of your company with regular proactive business reviews.
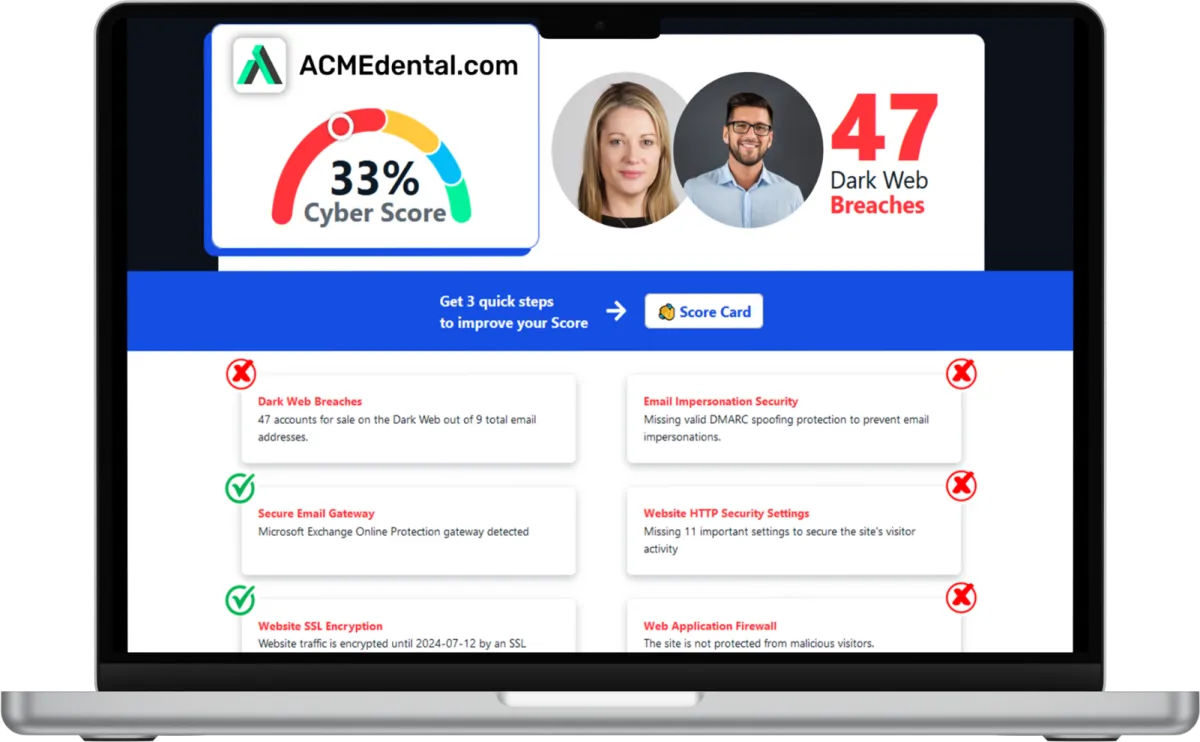
Want to see your Score? Get it in 30 seconds!
What Clients Say About Us
Managing Your Security Has Never Been Simpler

Discover Your Cyber Score
Start by assessing your Cyber Score to understand your business’s online security. This score provides clarity, replacing uncertainty with insight, so you know exactly where you stand and what needs improvement.

Create Your Cyber Roadmap
Use your Cyber Score to develop a clear, actionable Cyber Roadmap. This plan highlights vulnerabilities and provides precise steps to strengthen your security, saving you time and resources. Schedule a meeting with Big Water Tech so we can help you create a clear, strategic path to cyber resilience.

Enhance Your Security
Put your Roadmap into action with a step-by-step approach to stronger protection. Demonstrate your commitment to safeguarding customer data while equipping your IT team with a focused, cost-effective security strategy.

Want to see your Cybersecurity Score? Get it in 30 seconds!
The More You Know...
Our blog shares practical guidance, expert takes, and real-world lessons drawn from the front lines of IT services. Stay informed, stay protected, and make smarter decisions for your business.

Half of Staff Have Too Much Access to Data: The Hidden Insider Risk in Michigan SMBs
Here’s a question every Michigan business owner should ask:
Do you know exactly who in your firm can access your critical data right now?
And maybe the tougher follow-up:
Do they actually need that access to do their job?
For most accounting, legal, and medical practices across Michigan, the honest answer is probably “not sure.” Access tends to get set up once, during onboarding or system setup, and then forgotten. But that’s exactly where trouble begins.
📹 Watch: Half of Staff Have Too Much Access to Data (Tech Update)
In Big Water Tech's newest video Laura explains why “privilege creep” is one of the most overlooked business risks and how to fix it.
The Hidden Risk Inside Your Own Walls
New research shows that nearly half of employees have access to far more data than they should.
And that’s not just an IT oversight it’s a major business risk.
When too many people can see too much information, the problem isn’t just about malicious insiders. It’s about accidents waiting to happen. A single misdirected email, file upload, or permissions mistake can open the door to breaches, compliance violations, and costly insurance claims.
This kind of exposure is known as “insider risk.”
It’s the risk created by the very people who keep your business running—employees, contractors, even vendors with system access. Most insider risks aren’t intentional. They’re simply the byproduct of growth, turnover, and outdated access management.
How “Privilege Creep” Happens
Over time, employees accumulate access they no longer need.
They change roles, get added to new systems, or start using new tools and no one revokes the old permissions.
This slow build-up is called “privilege creep.”
Think of it like giving someone a master key because it’s convenient and then forgetting they still have it years later.
Even worse? Research shows nearly half of businesses admit that ex-employees still have system access months after leaving.
That’s like leaving the keys to your office in the hands of someone who doesn’t work there anymore.
The Fix: “Least Privilege” and “Just-in-Time” Access
The good news is that this risk is entirely preventable.
The first step is adopting what cybersecurity frameworks like CIS Controls v8.1 and NIST CSF 2.0 call the principle of least privilege. That means every employee only gets access to the systems and data they truly need—nothing more.
For temporary needs, use “just-in-time” access granting permissions only for a set period or specific task. Once the job’s done, access automatically expires.
And don’t forget the offboarding process. When someone leaves the company, remove all access immediately, email, cloud storage, practice management, and any shared credentials. One missed account can turn into a compliance audit nightmare.
Why It Matters for Compliance and Insurance
If your firm handles financial records, PHI, or legal client data, managing access isn’t just best practice it’s a compliance and insurance requirement.
Accounting firms: AICPA and cyber liability insurers now expect documented access reviews.
Law firms: The ABA Model Rules link client confidentiality to proper access control.
Medical practices: HIPAA’s Security Rule specifically requires role-based access and termination procedures.
Failing to manage access properly can lead to denied insurance claims or higher premiums even if no breach occurs.
Keeping It Simple (and Secure)
Today’s world of cloud tools, AI integrations, and remote work makes access management more complex but not impossible. With the right IT partner, you can:
Automate access reviews and removals
Track permissions across cloud and local systems
Align with CIS and HIPAA standards
Prove compliance to auditors and insurers
The goal isn’t to slow your team down, it’s to protect your data, your clients, and your firm’s reputation.
Because when you know exactly who has access to what, you’re not just securing systems, you’re safeguarding trust.
Need to find out where your firm stands?
Start with your Cyber Score or schedule a discovery meeting.
We’ll help you tighten access, align with compliance, and keep IT simple.
Our Services
Simple IT Management & Support
BIGview offers proactive management of technology assets on a subscription basis. BIGview is a service based offering designed specifically for your organization's requirements.
Hosted Voice
Desktop & Mobile App, SIP Firewall, and Service Management with flexible VoIP service. Powerful call control on a local business number you can access from anywhere.
Disaster Recovery & Backup
An automated data backup and restore system providing powerful tools to protect your organization's data. It doesn’t require any human assistance beyond the initial installation.
Managed Cloud Environment
Protecting your data is incredibly important. Our BIGcloud Server is highly secure, extremely reliable, easy to scale, and has simple and affordable pricing.
Managed File Sharing
BIGshare Managed Cloud Sharing is a secure, HIPAA & PCI compliant solution. Our BIGshare comes standard with backup and DRaaS all with unlimited storage for one simple price.
Managed Security
BIGprotect is a comprehensive fully-managed security solution. It provides a powerful way to protect your organization’s network .
Voice & Data Protection
BIGguard is a protection plan for your voice and data communications equipment. It provides a powerful way to protect your organization’s voice and data investment.
Security Assessment & Reporting
Elevate your security posture with our assessment and reporting solutions. Gain comprehensive insights into your organization's security landscape.
Take IT Off Your Plate...
Spend less time on IT problems and more time growing your business. Let’s get to know each other and determine how our partnership could grow. With us on your side, you can develop a strong barrier against cybercrime, stronger communication strategies, and a better technology plan for the future.
Call (248) 220-7714 today or fill out the form below to schedule your appointment. We’re ready to jumpstart your IT journey.



























